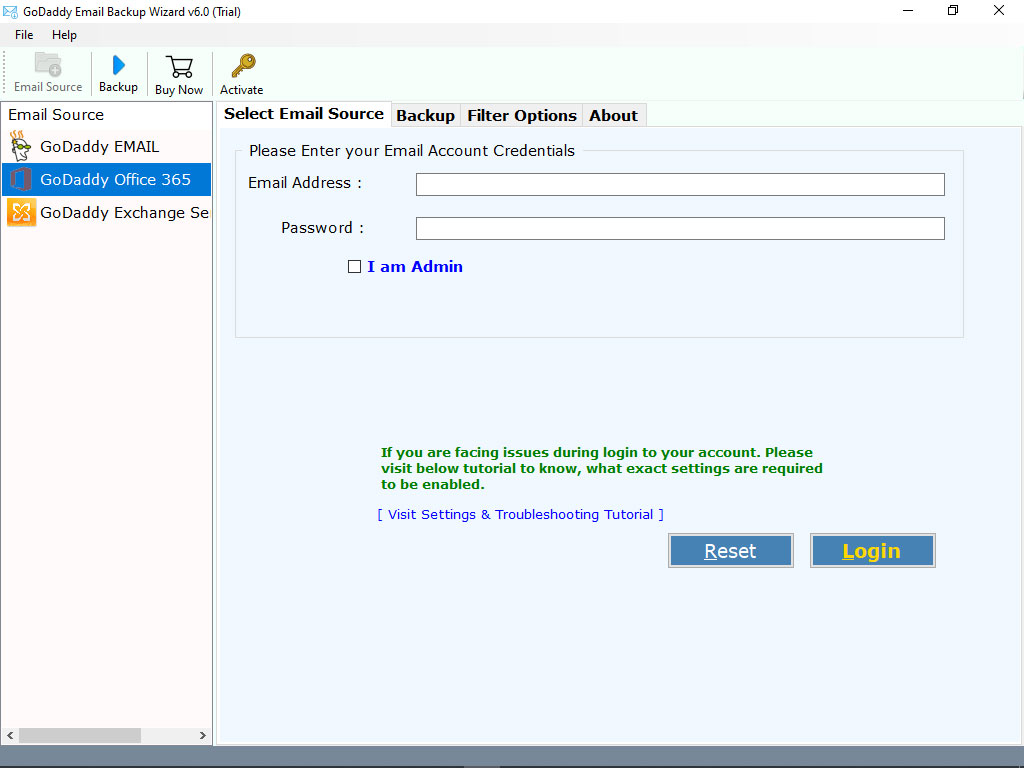
Programming Internet Email: Mastering Internet Messaging Systems: David Wood: 0636920924791: Amazon.com: Books
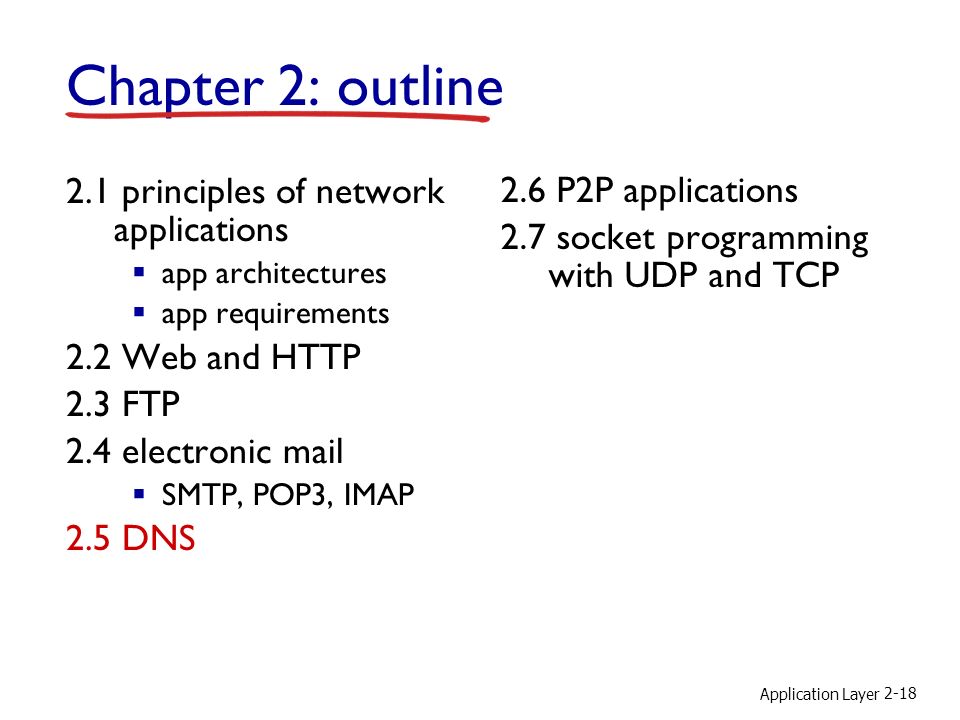
Application Layer 2-1 Chapter 2: outline 2.1 principles of network applications app architectures app requirements 2.2 Web and HTTP 2.3 FTP 2.4 electronic. - ppt download

Programming Internet Email: Mastering Internet Messaging Systems: David Wood: 0636920924791: Amazon.com: Books

Email encryption and signing | Email encryption can significantly improve your account security. Learn how to add certificates and how to protect your privacy. | By eM Client | Facebook

Email Address Mutation for Proactive Deterrence Against Lateral Spear-Phishing Attacks | SpringerLink

![What's the best email app for iPhone? [Updated for 2022] - 9to5Mac What's the best email app for iPhone? [Updated for 2022] - 9to5Mac](https://9to5mac.com/wp-content/uploads/sites/6/2019/03/Edison-Mail.png?w=1000)