GitHub - stevdza-san/USB-Stealer-Linux-OS: Well this USB stealer is not the same as in Windows OS, because on Linux you don't have permission to run scripts direct from USB. That's why you would

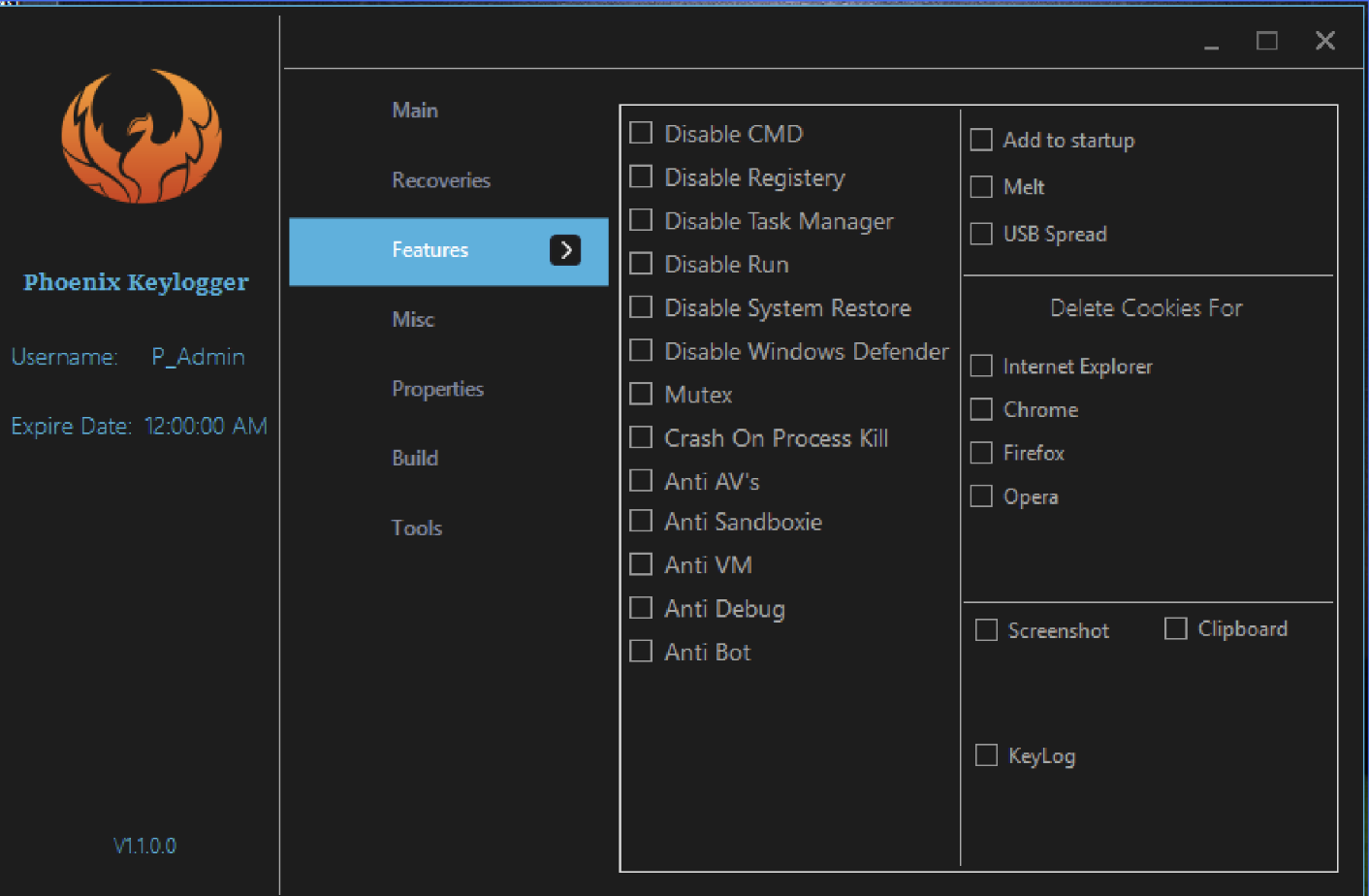
USB Stealer, Just like those unrealistic movies and TV shows, except this one's real. - Leewardslope







/cdn.vox-cdn.com/uploads/chorus_asset/file/23949203/226141_rubberDucky.jpg)