How to Build a Pumpkin Pi — The Rogue AP & MITM Framework That Fits in Your Pocket « Null Byte :: WonderHowTo
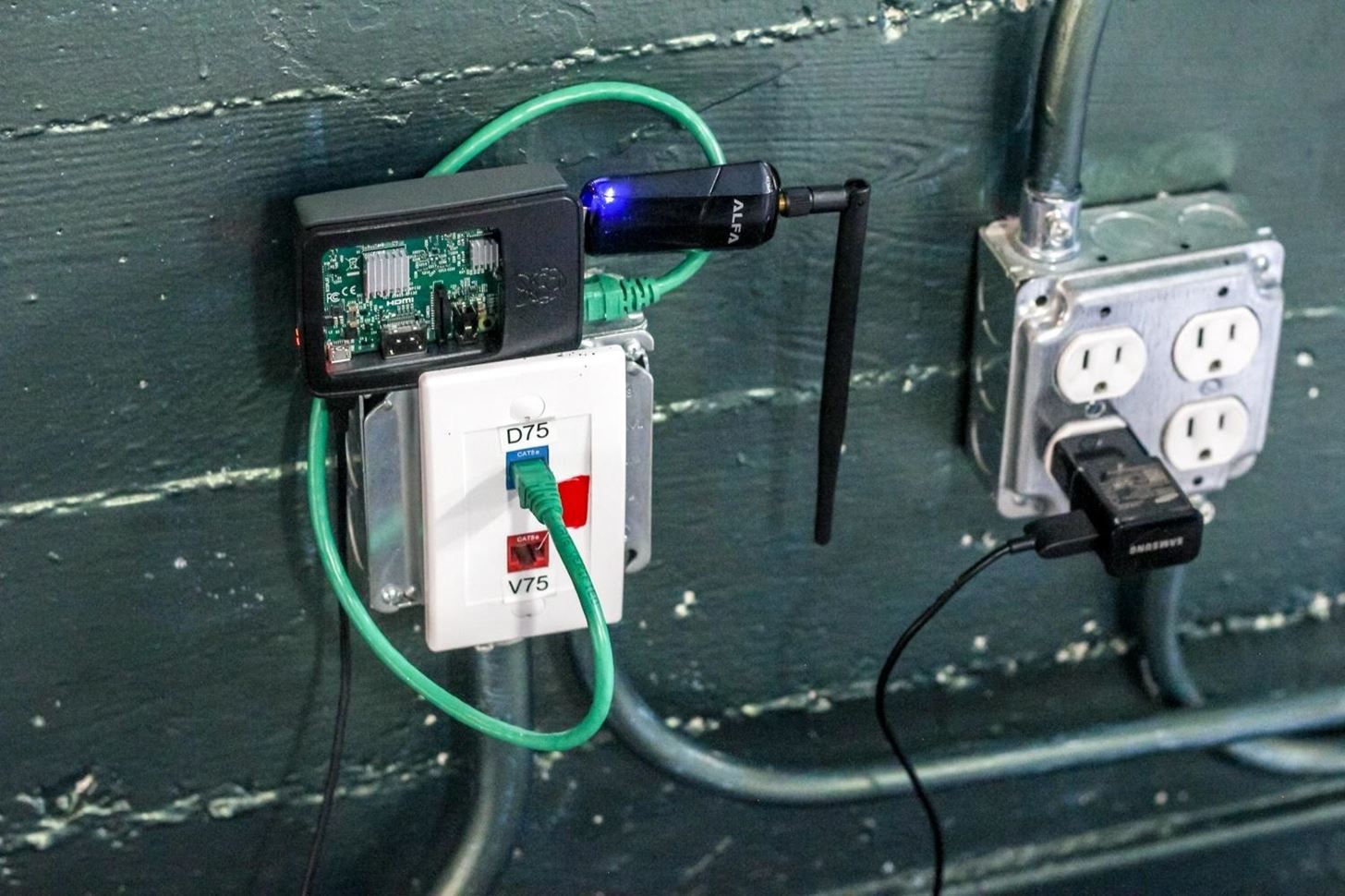
How to Build a Pumpkin Pi — The Rogue AP & MITM Framework That Fits in Your Pocket « Null Byte :: WonderHowTo

RaspberryPi – How to solve the SSH warning: WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! – El Bruno

Penetration Testing with Raspberry Pi: Muniz, Joseph, Lakhani, Aamir: 9781784396435: Amazon.com: Books